Creating the SoftNAS S3/EBS IAM Role for AWS
About IAM
AWS Identity and Access Management is a web service that enables Amazon Web Services (AWS) customers to manage users and user permissions in AWS. The service is targeted at organizations with multiple users or systems that use AWS products such as Amazon EC2, Amazon RDS, and the AWS Management Console. With IAM, you can centrally manage users, security credentials such as access keys, and permissions that control which AWS resources users can access.
Without IAM, organizations with multiple users and systems must either create multiple AWS accounts, each with its own billing and subscriptions to AWS products, or employees must all share the security credentials of a single AWS account. Also, without IAM, you have no control over the tasks a particular user or system can do and what AWS resources they might use.
IAM addresses this issue by enabling organizations to create multiple users (each user is a person, system, or application) who can use AWS products, each with individual security credentials, all controlled by and billed to a single AWS account. With IAM, each user is allowed to do only what they need to do as part of the user's job.
Creating the IAM Role for SoftNAS
To create an IAM role using the IAM console
1. From Amazon AWS console, click on IAM.
The IAM Console is displayed.
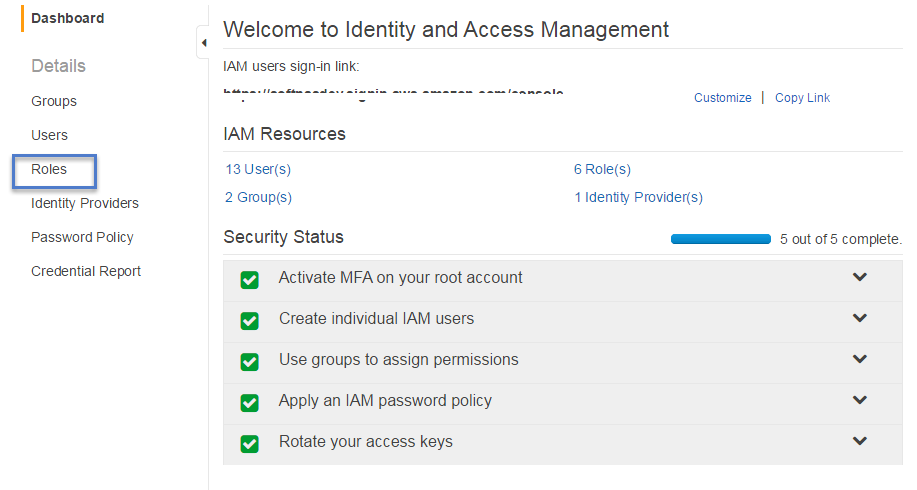
2. In the navigation pane, click Roles, and then click Create New Role.
3. On the Set Role Name page, enter a name for the role as SoftNAS_DISKS_IAM for s3/ebs
disk access and click Next Step. ( DO NOT use any other role name and its case sensitive)
4. On the Select Role Type page, click Select next to Amazon EC2.
5. On the Set Permissions page, Select “Custom Policy” and click on select.
6. On the second Set Permissions page, enter any name for policy and paste the following
template inside the “Policy Document” text box.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1411793193000",
"Effect": "Allow",
"Action": [
"ec2:AttachVolume",
"ec2:CreateSnapshot",
"ec2:CreateVolume",
"ec2:DeleteSnapshot",
"ec2:DeleteVolume",
"ec2:Describe*",
"ec2:DetachVolume",
"ec2:EnableVolumeIO",
"ec2:ModifyVolumeAttribute",
"s3:CreateBucket",
"s3:Delete*",
"s3:Get*",
"s3:List*",
"s3:Put*"
],
"Resource": [
"*"
]
}
]
}